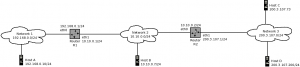
¿ Qué comandos serían necesarios ejecutar para que un sistema Linux pudiese sustituir el encaminador R2 mostrado en el diagrama ? Asume todos aquellos datos que necesites para realizar el ejercicio (nombre de interfaces, gateway, etc)
Previous Steps
Enable IP Forwarding
Temporal:
echo 1 > /proc/sys/net/ipv4/ip_forward
Permanent:
vim /etc/sysctl.conf
changue the value of net.ipv4.ip_forward = 1
sysctl -p /etc/sysctl.conf # enable changues
Configuring network intefaces
Temporal:
ifconfig eth0 down
ifconfig eth0 10.10.0.2 netmask 255.255.255.0 up
ifconfig eth1 downifconfig eth1 200.3.107.1 netmask 255.255.255.0 up
Persistent:
on debian: edit /etc/network/interfaces like this
auto lo
iface lo inet loopback
iface eth0 inet static
address 10.10.0.2
netmask 255.255.255.0iface eth1 inet static
address 200.3.107.1
netmask 255.255.255.0
red hat and derivates: edit /etc/sysconfig/network-scripts/ifcfg-<interface name>
Device eth0 file /etc/sysconfig/network-scripts/ifcfg-eth0
DEVICE=”eth0″
IPADDR=10.10.0.2
METMASK=255.255.255.0
NETWORK=10.10.0.0
BROADCAST=10.0.0.255
ONBOOT=yes
BOOTPROTO=none
USERCTL=no
Device eth1 file /etc/sysconfig/network-scripts/ifcfg-eth1
DEVICE=”eth1″
IPADDR=200.3.107.1
METMASK=255.255.255.0
NETWORK=200.3.107.0
BROADCAST=200.3.107.255
ONBOOT=yes
BOOTPROTO=none
USERCTL=no
Option 1: Using Static Routing
temporal:
#from network 2 to network 3 assumed not necessary
#from network 3 to network 2 assumed not necessary
#from network 3 to network 1
ip route add 192.168.0.0/24 via 10.0.0.1 dev eth0
persistent:
on Debian
edit /etc/network/interfaces
write this at after the interfaces setup
up route add 192.168.0.0/24 via 10.0.0.1 dev eth0
on Fedora
edit /etc/sysconfig/network-scripts/route-<device>
GATEWAY0=10.0.0.1
NETMASK0= 255.255.255.0
ADDRESS0=192.168.0.0
if you want to add more routes increment the numbers next to GATEWAY, for example: GATEWAY1=10.0.0.2 NETMASK1= 255.255.255.0 ADDRESS1=192.168.30.0
Pros
- No extra processing and added resources as in the case of dynamic routing protocols
- No extra bandwidth requirement caused by the transmission of excessive packets for the routing table update process
- Extra security by manually admitting or rejecting routing to certain networks
Cons
- Network Administrators need to know the complete network topology very well in order to configure routes correctly
- Topology changes need manual adjustment to all routers something which is very time consuming
Option 2: Using NAT
Basically NAT works like static routing but changes the output ip maintaining a internal
temporal:
# delete old configuration, if any
#Flush all the rules in filter and nat tables
iptables –flush
iptables –table nat –flush# delete all chains that are not in default filter and nat table, if any
iptables –delete-chain
iptables –table nat –delete-chain# Set up IP FORWARDing and Masquerading (NAT)
iptables –table nat –append POSTROUTING –out-interface eth0 -j MASQUERADE
iptables –append FORWARD –in-interface eth1 -j ACCEPT
permanent:
store the rules into the ip tables into a rules set
Pros
same that static plus
It also benefits in a security sense as attackants can’t target a computer directly, they have to first get past the router.
Cons
- Network Address Translation does not allow a true end-to-end connectivity that is required by some real time applications. A number of real-time applications require the creation of a logical tunnel to exchange the data packets quickly in real-time. It requires a fast and seamless connectivity devoid of any intermediaries such as a proxy server that tends to complicate and slow down the communications process.
- NAT creates complications in the functioning of Tunneling protocols. Any communication that is routed through a Proxy server tends to be comparatively slow and prone to disruptions. Certain critical applications offer no room for such inadequacies. Examples include telemedicine and teleconferencing. Such applications find the process of network address translation as a bottleneck in the communication network creating avoidable distortions in the end-to-end connectivity.
- NAT acts as a redundant channel in the online communication over the Internet. The twin reasons for the widespread popularity and subsequent adoption of the network address translation process were a shortage of IPv4 address space and the security concerns. Both these issues have been fully addressed in the IPv6 protocol. As the IPv6 slowly replaces the IPv4 protocol, the network address translation process will become redundant and useless while consuming the scarce network resources for providing services that will be no longer required over the IPv6 networks.
Option 3: Using RIP
Rip is a distance routing protocol, is more flexible that using static routers and necessary if the number of subnets grows. Do you want to fight against hundred of rules? or assume the risk of downtime’s created by a router malfunction?
install zebra
permanent:
edit the /etc/zebra/ripd.conf file
redistribute connected
version 2
ip rip authentication string “max 16 characters”
router rip
network 10.10.0.0/24
network 200.3.107.200/24
pros
- Easy to configure and use
- V2 supports VLSM and CIDR
cons
- Converges slowly on large networks
- Doesn’t recognize bandwidth of links
- Doesn’t support multiple paths for the same route
- Routing updates can require significant bandwidth because the entire routing table is sent
- Prone to routing loops
Option 4: Using OSPF (Open Shortest Path First)
OSPF is a routing protocol that uses the Dijkstra algorithm for get the quickest way. into a set of subnets where the routers are connected at different speeds could work better than R.I.P.
install zebra
add the necessary VTY in /etc/services
zebrasrv 2600/tcp # zebra service
zebra 2601/tcp # zebra vty
ospfd 2604/tcp # OSPFd vty
ospf6d 2606/tcp # OSPF6d vty
edit zebra.conf file
hostname R2
password zebra
enable password z3bRa
log file /var/log/zebra/zebra.log
!
interface eth0
description Network 2
ip address 10.10.0.2/24
!
interface eth1
description Network 3
ip address 200.3.107.1/24
start zebra service
/usr/sbin/zebra –dk
/usr/sbin/ospfd –d
Telnet to port 2604 on the local machine to begin the OSPF configuration and type enable in order to get privileged mode
the next step will be announce the networks that we want to publicity in out networks
R2:~# telnet 0 2604
Trying 0.0.0.0…
Connected to 0.
Escape character is ‘^]’.
Hello, this is zebra (version 0.84b)
Copyright 1996-2000 Kunihiro Ishiguro
User Access Verification
ospfd> enable
Password:
ospfd# configure terminal
ospfd(config)# router ospf
ospfd(config-router)# network 10.10.0.0/24 area 0
ospfd(config-router)# passive-interface eth0
ospfd(config-router)# network 200.3.107.0/24 area 0
ospfd(config-router)# passive-interface eth1
ospfd(config-router)# end
ospfd# write file
Configuration saved to /etc/zebra/ospfd.conf
pros
- Scalability – OSPF is specifically designed to operate with larger networks.
- Full subnetting support – OSPF can fully support subnetting
- Hello packets – OSPF uses small hello packets to verify link operation with out transferring large tables
- TOS routing – OSPF can route packets by different criterion based on their type of service field
- Tagged routes – Routes can be tagged with arbitrary values, easing interoperation.
cons
- very intensive processor
- maintaining multiple copies of routing information, increasing the amount of memory needed
- OSPF can be logically segmented by using areasnot as easy to learn as some other protocols
- if an entire network is running OSPF, and one link within it is “bouncing” every few seconds, then OSPF updates would dominate the network by informing every other router every time the link changed state.
sources:
http://www.techrepublic.com/article/use-zebra-to-set-up-a-linux-bgpospf-router/1047843
http://www.trainsignaltraining.com/ip-addressing-routing-default-static-routing
http://ipv6.com/articles/nat/NAT-Pros-and-Cons.htm
www.techrepublic.com/i/tr/one_offs/t063_preview.pdf
http://gotechsf.wordpress.com/2009/09/05/the-pros-and-cons-of-ospf-and-eigrp/
http://ipsit.bu.edu/sc546/sc441Spring2003/ospf/proscons.html